What’s Tor? Is Tor Better than VPN for Web Privacy & Security?

To disguise identity from ISP, government, advertiser, hacker etc., you can gain the benefit of Tor browser, a privacy tool trusted even by US Navy.
Tor is a free and open-source software project that’s initially developed and released by mathematician Syverson, computer scientists Roger Dingledine and Nick Mathewson in 2002. The very first person is just one team member of the Onion routing principle which Tor is based on. Therefore, they just called it “The Onion Routing project”, shortly known as TOR.

What Is Tor?
Tor, in a large sense, refers to a series of The Tor Routing project’s implementations, specifically Tor browser, Firefox/Tor browser attack, Tor messenger, some 3rd-party applications and security-focused operation systems, some of which are discontinued for subjective or objective reasons.
In a narrow sense, Tor is either regarded as the Tor browser or the anonymous communication approach online with Tor browser.
What Is Tor Browser and How It Works?
Tor browser is the flagship product of The Tor Project, with which any journalist, activist, whistleblower, law enforcement, and the average individual could use to hide IP address and achieve online anonymity, defending themselves against internet censorship and surveillance, and other limitations while browsing online, possibly realizing the true online freedom. Also, it’s commonly used as the browser to access the dark web.
| Tor browser supported operation system: | Windows, Mac OS X, Linux, Android |
| Latest version of Tor: | Version 11.0.14 (updated on June 7, 2022) |
| Tor browser supported languages (36): | English, Arabic, Czech, Croatian, German, Greek, Spanish, Spanish Argentines, Persian, French, Irish, Hebrew, Hungarian, Indonesia, Icelandic, Italiano, Japanese, Georgian, Korean, Lithuanian, Macedonian, Sindhi, Norwegian, Dutch, Polish, Portuguese-Brazil, Romanian, Russian, Swedish, Thai, Turkish, Vietnamese, Simplified Chinese, Traditional Chinese |
* Note: Tor Browser is unavailable for iOS devices now, and the developer suggests users in demand to use Onion Browser as the alternative.
How does Tor browser protect netizens from web action tracking, personal information collection, traffic analysis etc.?
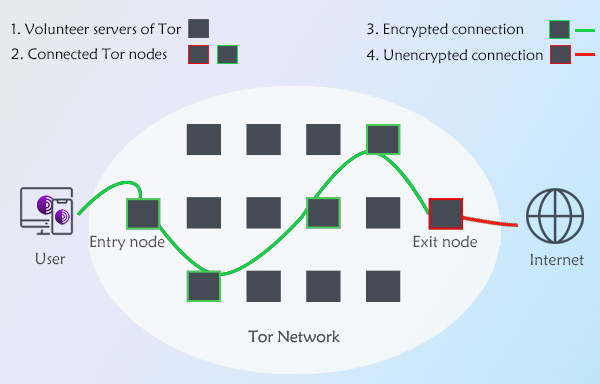
Firstly, it has its own overlay network to direct traffic, thus all traffic passed through the Tor network will be encrypted and concealed, including IP address, real-time location, and other personal information.
Then since the overlay network is made up by over 6000 volunteer-operated servers worldwide, instead of routing the traffic from user end to end server directly, each web request may walk through multiple relays (picked at random) between different servers to form a connection circuit to make sure the data is fully protected. Moreover, each relay only knows the relays that deliver data to and receives data from it, it’s impossible for either to know the full connection path.
At last, Tor Browser will by default clear the cookies and browsing history immediately after your browsing action, disabling the destination website or any other party to learn what you’re doing here except when you are running Tor to access the Internet.
Tor Browser not only helps protect user’s online privacy, by working in this way, it also enables you to unblock local network’s restrictions and access anywhere you want.
Advantages and Disadvantages of Tor Browser/Proxy
Below are some typical benefits and disadvantages of Tor Browser and Tor-proxy-enabled App.
| A General Look at Tor’s Pros and Cons | |
| Pros | Cons |
| Totally free to download and use | Slow connection because of multi-layer data transport |
| Access any website including the deep web | Certain websites block Tor access |
| Much safer than other browsers | The traffic is not encrypted in the exit node |
| Brower software has security vulnerability (especially for HTTP sites) | |
| Not support browser plug-in, incl. Flash, RealPlayer, QuickTime | |
| BitTorrent over Tor is unsafe and not suggested | |
| Open downloaded file within Tor is insecure | |
| Third-party will know you’re using Tor Browser | |
Tor has an excellent goal to move forward to, just like the big slogan showing on its official homepage “Browse Privately. Explore Freely.” And it distinguishes itself from other proxies by passing traffic through 3 or more different volunteer servers and then the target Internet destination. That said, exactly, a general web proxy server simply transmits traffic via one single server. (>>see what is a proxy server)
However, “the road ahead will be long” because Tor is unable to get all anonymity problems fixed currently, like the general public wish.
Either web browsing with Tor Browser or running an app configured with Tor internet is safe. Nevertheless, even so, if you sign in to any account here or leave any personal information (e.g. name, email/address, telephone number) online, your cloak will go away. Similarly, the reason that Tor Browser doesn’t like all browser extensions still lies in the risk of IP leakage. As long as the extension’s part gets your IP address and footprint, the online privacy cracks.
What’s more, Tor Browser is only friendly to TCP streams but doesn’t work for UDP. By supporting SOCKS service, Tor allows any SOCKS-available app to make use of its internet by doing related HTTP/HTTPS proxy configurations inside. Unquestionably, HTTPS, thanks to traffic encryption, is more reliable than HTTP.
How to Use Tor to Stay Anonymous
Steps on how to use Tor Browser on PC and mobile:
1. Navigate to Tor’s official download page.
2. Pick the correspondent installer to download. As mentioned above, Tor works well with Windows, macOS, Linux and Android while has no package here for iOS and ChromeOS-based machines at present.
3. Verify Tor Browser’s digital signature (only for Windows/Mac/Linux, optional yet recommended | signature guide).
4. When the download is completed, click to set the client up on your device.
5. Launch Tor Browser and enjoy privacy and freedom online.
Some details by the way: Tor Browser, since version 6.0.6, has automatically set DuckDuckGo as the default search engine under Search panel. And the Security Level under Privacy & Security settings is selected as “Standard”. If you’d like to switch DuckDuckGo to Google, or level up the security, feel free to navigate to the right place to make it happen.
Use Tor Internet at system level: Tor Browser only routes and safeguards the traffic within its own browser, which means all the other browser & app traffic are unable to enter into Tor internet and get protection. To have all traffic go through Tor network, Tor project officially comes up with a portable Tor-network-enabled operation system called Tails live to take along everywhere, avoiding surveillance, censorship etc. on Windows/Mac/Linux PC easily.
Tor VS. VPN, Which One is Better?
VPN is a mainstream method to shield internet privacy and security, especially when connecting to a public network. Since VPN routes all traffic via the highly encrypted tunneling from the very beginning to ending, VPN’s undoubtedly more secure than Tor.
As to product features, both Tor and VPN can be leveraged to hide IP address, keeping user away from censorship/monitoring/hacking, and remove geo-locking of certain web resources. But to a large degree, VPN is superior to Tor because its rich servers can be applied for any kind of online behaviors like web browsing, P2P file sharing, BitTorrent downloading and streaming while Tor is more suitable for website surfing. On one hand, Tor’s relatively slow speed is bound to be negative for streaming. On the other hand, Tor’s team has been saying “don’t torrent over Tor” for a long time for its network are incompetent for the load.
In short, if you are looking for a long-term approach for online privacy, security, and freedom, VPN service like PandaVPN is more recommended.
PandaVPN – a slick & cross-platform VPN with over 3000 high-speed servers located in 73 countries and 127 cities worldwide. Zero log, zero personal information leakage, 100% privacy protection, and the highest-level of web security!
VPN over VPN, Is It OK to Use Them Together?
Many users still wonder whether it’s possible to use Tor browser with a VPN. The answer is surely YES.
Combining Tor with VPN does increase online privacy and security. In this way, all traffic is locked so tightly that nobody can catch your identity, even including you are using the Tor browser thing. Tor doesn’t recommend the green hands to use Tor and VPN simultaneously just because they most probably have no idea on how to configure them well.
However, despite VPN adding an extra privacy and security layer to your web behavior on Tor, it’s impossible for Tor to get rid of its born shortcomings, say not fast connection speed, unsafe with browser plugin/BitTorrent/streaming etc. From this point of view, if Tor is not a must-have browser to visit certain sites, you can simply rely on a VPN to convoy your privacy, safety and unblock contents with other general browsers like Chrome, Firefox, Safari, and so forth.
The Bottom Line
After figuring out what is Tor, how does Tor work, its pros and cons, and the relationship with VPN, you must know exactly on how to maintain the online privacy and get out of the tracking from government, ISP, hacker, search engine, etc. Only with a VPN running in the background, your Tor journey can be totally hidden.
At last, many claim Tor Browser as the cyber heaven of illegal activity because a group of criminals engages themselves in drug trafficking, child pornography, and arms trading with Tor. Is the action 100% untraceable? If it really was, there would not be so many offenders being arrested and put into prison. So, don’t hold the fluke mind, just use Tor/VPN by following your country or region’s law.
 Vic Knott
Vic Knott  2022.05.18
2022.05.18