VPN Encryption Guide – Cover Everything You Need to Know

VPN creates a virtual tunnel for you to access the internet. Inside the tunnel, all data you send and receive is encrypted. VPN encryption secures your personal information and online data against snoop from hackers, advertisers, ISPs, and the government.
How does VPN encryption work? Why is it important? Is it safe? Can VPNs be hacked even with encryption? Read the guide below to figure out.

What are the main VPN encryption types?
Here are the main types of encryption algorithms you can see VPN providers use.
- 1. Triple DES
DES stands for Data Encryption Standard. As an advanced version of DES, Triple DES is a symmetric algorithm that can be used for encrypting data. The original DES has been overcome by hackers. Now Triple DES is still being used by some VPN providers.
Rather than using a single key as in DES, Triple DES employs three 56-bit keys. In short, Triple DES provides much stronger encryption than DES. But compared with the Advanced Encryption Standard (AES), Triple DES is less secure.
- 2. Blowfish
Blowfish was created to replace DES, which is also a symmetric algorithm that splits data into blocks of 64 bits and encrypts each block separately. Blowfish providers a variable-length key, from 32 to 448 bits, making it ideal for public use.
In comparison to DES, Blowfish is much safer at the expense of speed.
- 3. Twofish
Twofish is the newer version of Blowfish, offering stronger encryption than Blowfish. As an asymmetric algorithm, Twofish requires only one key that has a length of 256 bits. Fast speed and enough security make it widely used with both hardware and software.
- 4. RSA
RSA is an asymmetric algorithm that uses a pair of keys to encrypt data. There is a public key to encrypt an original set of data, and then a private key to go on to encrypt it. That means it will take a great deal of time for hackers or other cybercriminals to make sense of the data that is being transferred.
- 5. ECC
ECC (Elliptic Curve Cryptography) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller and more efficient cryptographic keys. Its 256-bit key strength equals that of a 3072-bit RSA key.
The shorter key length means less processing power to encrypt and decrypt data, making ECC a good fit for mobile devices. A rising VPN provider, PandaVPN uses ECC to encrypt your privacy and browsing history.

- 6. AES
AES is short for Advanced Encryption Standard, which is the strongest symmetric algorithm. Supporting 128-bit, 192-bit, and 256-bit keys, AES is very popular with VPN providers to improve security. The longer the key length, the higher the security level.
Why is VPN encryption important?
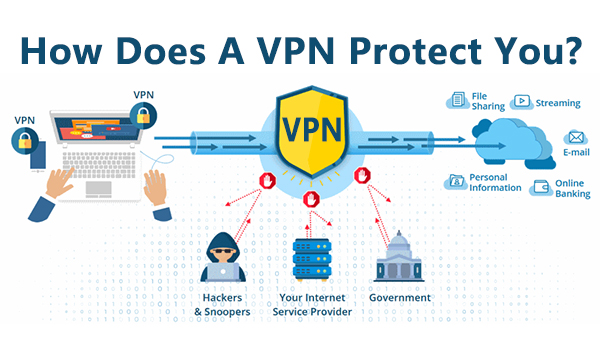
As we all know that VPNs are safeguards for privacy security. And VPNs are able to protect privacy because of encryption algorithms. Encryption is the process through which data is encoded so that it remains hidden from hackers, advertisers, ISPs, and the government.
VPN encryption makes sure hackers or other cybercriminals can’t eavesdrop on your Internet connections when you use public Wi-Fi. Your personal information and sensitive data like credit card numbers, bank account details, and login credentials are unreadable for them.
Besides that, your internet activities can’t be monitored by your government, ISP, and advertisers.
It prevents governments from forcing censorship down your throat. Your ISP can’t easily throttle your bandwidth since they can’t see what you do online. Advertisers can’t track you so that they can’t bother you and get you spammed with personalized ads.
How does VPN encryption work?
To encrypt data, an encryption key uses an encryption algorithm to encode plaintext or readable data into unreadable data or ciphertext.
Simply put, when you run a VPN and connect to a VPN server, your connection requests are encrypted before they are sent to the server.
Then, they are decrypted by the server, forwarded to the Internet, and the requested data is encrypted once more when the server receives it before it’s sent back to your device.
Once received, the data is decrypted by the VPN client so that you can view it.
Can VPNs be hacked even with encryption?
The truth is VPNs can also get hacked even with encryption. Not all VPNs are given strong and secure encryption. There are a handful of poor VPNs.
Poor VPN services can only offer a poor level of encryption, which is unavailable to shield your sensitive information and browsing history. Their unstable connections make it impossible for you to stream. What you can expect are only unlimited lags.
It’s not worth spending a penny on these VPNs. Besides the above-mentioned poor VPNs. Free VPNs are even much easier to be hacked than paid VPNs.

Free VPNs are not safe enough, usually coming with weak encryption that can’t protect your data security. Even worse, ads included in free VPNs might pose a threat to your online privacy. Thus, free VPNs are not recommended if you care much about digital privacy.
Conclusion
When you are shopping for a VPN, VPN encryption should be an important consideration. There is a variety of data encryption algorithms. Always remember to choose stronger encryption. It keeps your privacy and data security better.
PandaVPN is based on ECC encryption, which is the strongest asymmetric encryption algorithm. What’s more, PandaVPN is a true zero log VPN, offering a random string of numbers as your account and recording no account details, payment info, and all of your online activities. How about giving it a try >
 Tony Bennett
Tony Bennett  2021.10.28
2021.10.28